What are privacy-enhancing technologies?
Privacy-enhancing technologies (PETs) are tools and methodologies designed to protect personal data and uphold user privacy rights in digital environments. PETs help organizations navigate the complex privacy landscape while ensuring the safety and integrity of user data.
The FTC’s perspective on PETs emphasizes the gradual shift toward minimizing or even eliminating user data access: “On one end of the spectrum, a company has access to all of an individual’s private information and relies on internal policies and procedures to ensure this information is not misused or breached. On the other end of the spectrum, there are technologies which allow a company to offer products and services without ever having access to a user’s data. PETs are approaches that allow companies to move towards the latter end of the spectrum — some reach the end goal of a company truly not having access to the data of any individual, and others reside in the middle, where they limit access but still have some reliance on a company’s policies and practices.”
Examples of PETs
PETs encompass a wide range of tools and techniques, including those designed to enhance data security, privacy, and compliant data processing practices. Examples include:
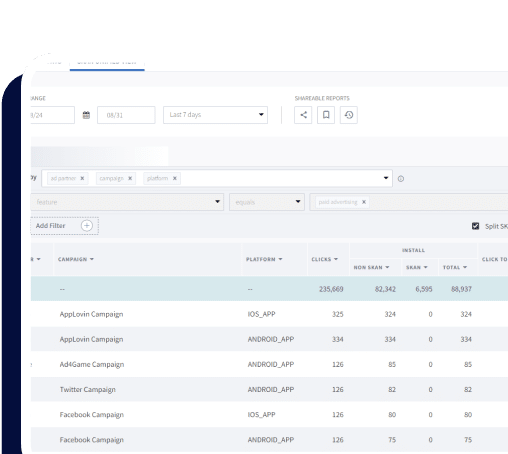
Data clean rooms: Perhaps the best-known PET use case, data clean rooms facilitate the aggregate, anonymization, and analysis of first-party data from various sources in a secure environment. Their primary application is data sharing for advertising and analytics purposes.
End-to-end encryption (E2EE): E2EE is a secure communication method that protects data from unauthorized access or interception by third parties. The cryptographic technique safeguards sensitive information during transmission and storage from device to device, ensuring that only the intended parties can access encrypted data.
Pseudonymization: Pseudonymization replaces identifiable information with artificial identifiers, or pseudonyms, to reduce the risk of reidentification. Anonymizing personal data enables organizations to process and analyze data while minimizing privacy risks.
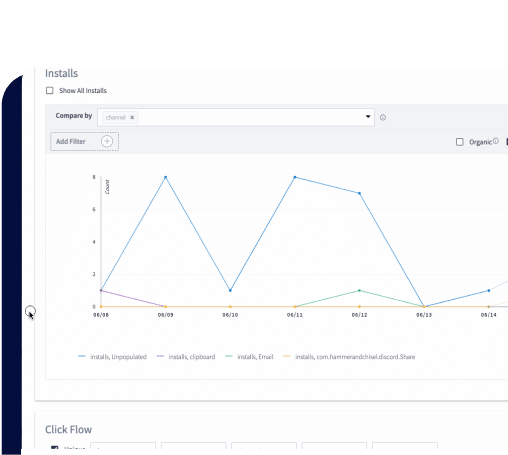
Differential privacy: Differential privacy enables organizations to analyze datasets while preserving the privacy of individual data points. It adds noise or “randomness” to query results to prevent the disclosure of sensitive information while still allowing for analysis and insights.
Obfuscation: Obfuscation introduces noise into datasets to protect sensitive information from unauthorized access or misuse. By obscuring the meaning or structure of data, obfuscation enhances privacy protection during data analysis and processing. Unlike differential privacy, which focuses on protecting individual data points, obfuscation operates at the broader dataset level.
Trusted execution environment (TEE): A trusted execution environment (TEE) is a secure area within a device’s main processor that ensures confidential computing. It isolates code execution and data processing from the rest of the system, protecting it from unauthorized access and threats. Even if the operating system is compromised, the TEE keeps the data safe.
Blinding: Blinding is a cryptography technique that masks specific data points or attributes within a dataset, preventing organizations from identifying individuals or sensitive information.
Why do PETs matter now?
PETs aren’t new; they have existed for decades, but their relevance has surged in recent years. With the exponential growth of digital data — and growing concern over data breaches and sensitive data protection — organizations are struggling to leverage data insights while simultaneously protecting individual privacy. PETs offer a privacy-safe approach to tackle these challenges, in turn helping organizations and providers to:
- Foster trust: Investments in PETs signal to customers and business stakeholders, including partners, investors, and regulators, that an organization is committed to protecting user data. This helps build brand loyalty and strengthen customer relationships.
- Comply with data privacy regulations: Data protection laws, such as the General Data Protection Regulation (GDPR) in the European Union and the California Consumer Privacy Act (CCPA), have pressured organizations to rethink their data collection and usage practices. PETs have become useful tools for navigating the regulatory landscape, providing mechanisms to comply with evolving regulations and avoid penalties.
- Reduce risk: Data breaches have significant consequences for organizations, not only in terms of financial losses but also in damaging reputations and fracturing customer trust. PETs help mitigate the risk associated with user data collection, storage, and sharing by minimizing the likelihood of unauthorized access or misuse.
- Execute critical business functions: Finding the balance between user privacy and meeting business objectives can be difficult. PETs, in theory, are not just safeguards against data breaches; they enable brands to carry out operations, explore new avenues, and innovate without compromising user privacy.