BRANCH FRAUD PROTECTION
Protect your ad spend
Rely on our extensive fraud mitigation expertise for cutting-edge protection measures
Request a demoSafeguard your budget with dynamic fraud defense
Protect your ad spend and create custom event-level restrictions based on any attribute. Our proprietary algorithms keep you protected as fraud patterns evolve.
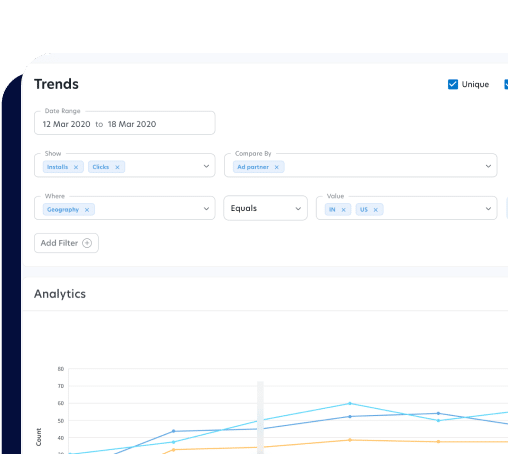
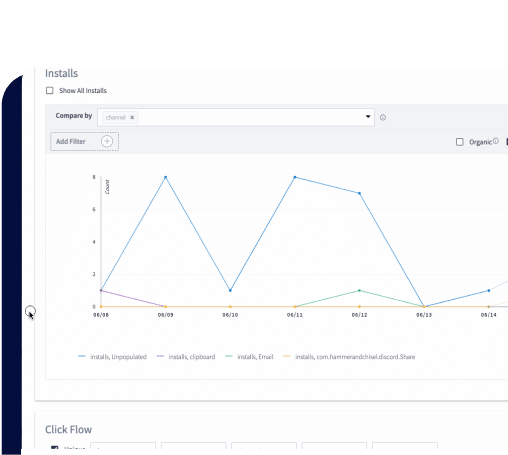
Detect and report suspicious activity with an intuitive dashboard
Easily identify unusual patterns in data, keeping anomalies separate from your healthy ad spend analytics.
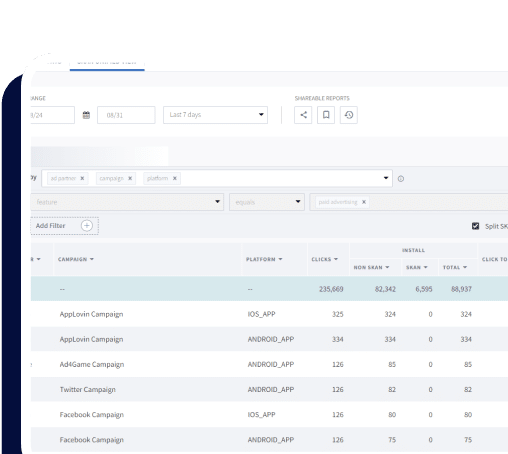
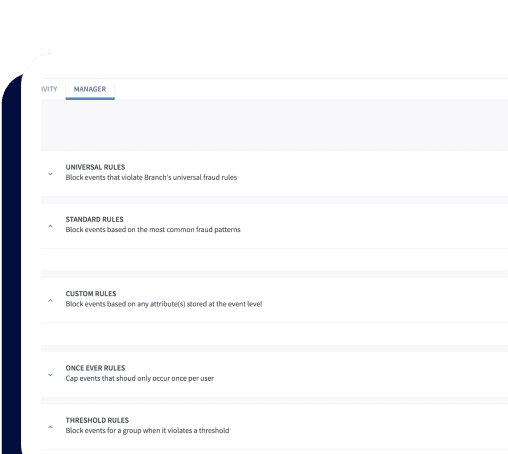
Protect against known fraud patterns with industry-standard blocking rules
Continuously block suspicious attributions across browsers and devices with proprietary algorithms and fraud blocking logic.
Identify and prevent new fraud with advanced detection techniques
Block fraud with statistical methodologies and anomaly detection while ensuring accurate attribution that respects user privacy.
Detect and block fraud before
it happens
Fake devices or click farms
Fraud technique:
Use emulators and device farms to generate fraudulent clicks.
Detection strategy:
Block IP addresses that lead to multiple conversions originating from the same location. Monitor high click-to-install rates as this fraud method thrives when clicks lead to installs.
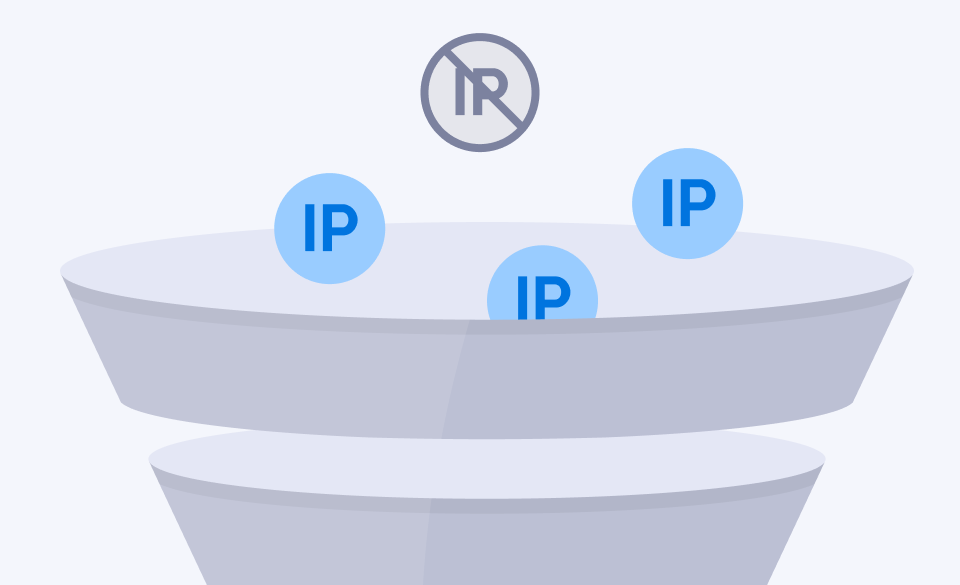
Install hijacking or click injection
Fraud technique:
Exploit a compromised app already on a device to detect installations and trigger a click just before launching a new app.
Detection strategy:
Look for short click-to-install times, as users typically open apps right after downloading them.
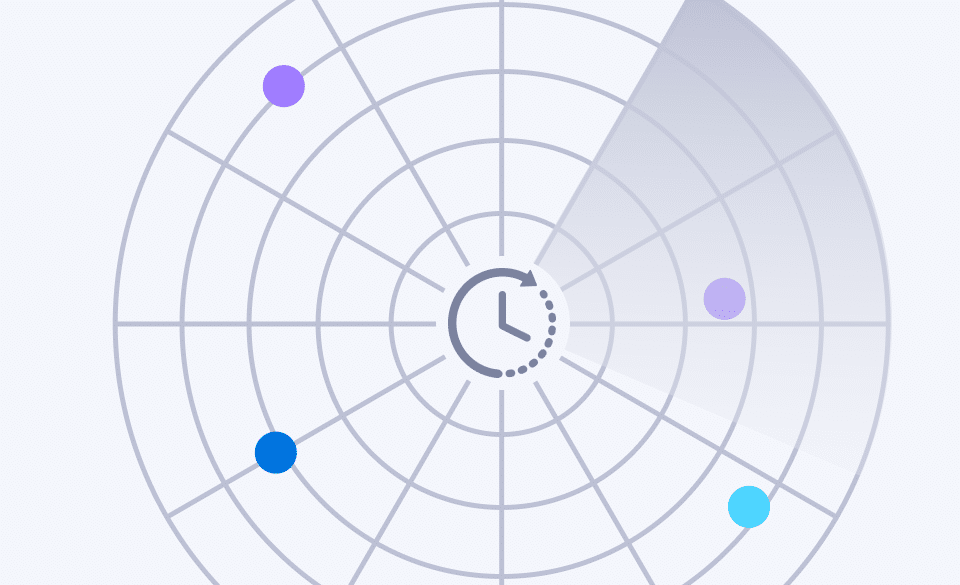
Click flooding
Fraud technique:
Generate millions of clicks by using random device IDs (IDFA or GAID) and hope that some of those users will install later.
Detection strategy:
Identify long click-to-install times that signify no legitimate connection between a click and an install.

Ad stacking
Fraud technique:
Layer dozens of ads on top of each other, leading to fraudulent clicks on ads that are not visible to the user.
Detection strategy:
Spot low click-to-install rates, as this fraudulent method generates an unusually high number of clicks.

Keys to preventing mobile ad fraud
Scalable, data-driven action
Relying on static, hard-coded blocking rules — that quickly become outdated — enables fraudsters to adapt to ever-evolving fraud patterns.
Our unique, cross-platform scale provides the necessary depth and breadth of data required to build resilient, scalable fraud detection models. We automate the detection of statistical anomalies across a vast pool of data signals to identify and block fraudulent patterns as they emerge.
Quality insights
Many attribution providers mark fraudulent attribution data as “organic.” This distorts healthy analytics and prevents customers from comparing traffic quality across their ad sources.
We provide clear visibility into suspicious data patterns, keeping them separate from healthy analytics in your Branch Dashboard. To preserve your attribution data, we proactively block attribution payouts and take action to remove fraudulent activity in real time, so you don’t have to worry about recovering losses.
Ready to fraud-proof your mobile advertising budget?
Mobile Ad Fraud Impacts and What To Do About It

Why You Need an MMP and Why Branch Is the Best Fit

How To Increase Your Mobile Conversion Rates in a Privacy-led World