What is click injection?
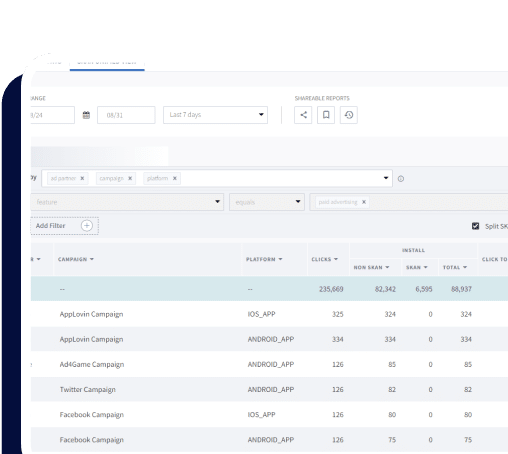
Click injection is a type of ad fraud where attackers inject fraudulent or unauthorized clicks on advertisements within mobile applications. This is generally done to manipulate click-through rates, inflate app and ad metrics, and ultimately generate illicit revenue from advertisers.
Click injection is similar in concept to click hijacking, where a legitimate click is replaced by a fraudulent click as the last touch before an install or purchase event.
How click injection works
- User A has a fraudulent app installed on her device — usually through a third-party app store. The fraudulent app is often a very basic app with some ads.
- When User A downloads a new e-commerce app to her device, all existing installed apps on her device are notified of this download event. This is a particular loophole with Android devices. iOS devices are less susceptible to click injection.
- If this e-commerce app is running an install advertising campaign, the fraudulent app could be participating too and therefore has the tracking codes. The download event triggers the fraudulent app to report a click from User A.
- Ads attribution services start tracing clicks in reverse chronological order when the new e-commerce app is opened the first time. The fraudulent click has all the correct matching on device IDs and track code, and will therefore be determined as the last-touch click. Fraudsters will then be rewarded the ad dollars associated with User A’s install.